This vulnerability with Airtag enables hackers to steal your Apple account
A security researcher says that Apple's "AirTag" makes it easy to phish people and steal their accounts, by letting hackers leave AirTag, and when an iPhone user who found it reports it, their account is hacked, according to a report in Tom's Guide. (tomsguide).
Airtag is a tracking device developed by Apple designed as a key finder, to help people find personal items (such as keys, bags, clothes, small electronic devices and vehicles) when they are lost.
Bobby Rauch, a Boston-area cybersecurity consultant, spoke in a blog for freelance security reporter Brian Krebs about how the hack occurred.
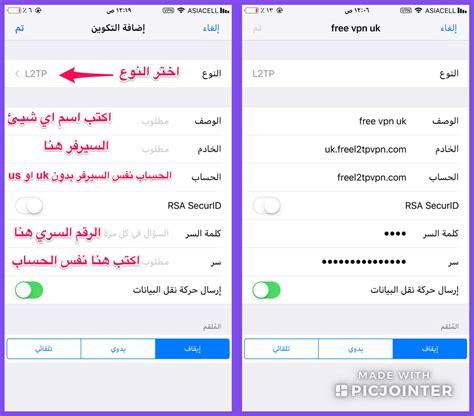
In a series of YouTube clips, Rauch showed how he could use off-the-shelf software to inject invisible text into the phone number field that an AirTag's owner fills in when Apple reports a missing AirTag.
An iPhone user who finds a missing Airtag wirelessly connects their iPhone, which in turn will force the iPhone to open a page on "found.apple.com" for that missing device.
Usually, this page found will contain information about contacting the lost legitimate owner of Airtag. But in this case, the hidden text will secretly redirect the victim's iPhone to a page that looks like the iCloud login page, but will actually be a phishing page ready to steal the victim's Apple username and password.


Rauch told Krebs that he told Apple about this vulnerability last June, but the vulnerability remained on Apple for 3 months while the company was investigating. After 3 months had passed—generally seen as long enough for a security researcher to wait before an uncorrected flaw was detected—Rauch reached out to Krebs.
Krebs contacted Apple for comment, and soon after Apple sent Rauch an email asking him not to discuss the vulnerability publicly. Apparently Rauch refused, telling Krebs that he had not been given a timetable on when the bug would be fixed, whether he would be credited with finding it, or whether he would get any kind of "bug bounty" at all.
Rauch told Krebs that correcting this problem simply involved blocking some characters from the page's entry fields that were found.
"It's an easy thing to fix," Rauch said. "Having said that, I imagine they (Apple) might also want to know how this was missed in the first place."
Tom's Guide said it has contacted Apple for comment, and will update this story when it receives a response.
How do you avoid this type of attack?
To protect yourself from this type of attack, be aware that you don't need to be signed in to iCloud or your Apple account to report a found Airtag.
You should also enable two-factor authentication to make it difficult to log into your Apple account for an attacker who doesn't own one of your Apple devices, even if that attacker has your Apple username and password.
If you believe your Apple ID has been phishing or otherwise stolen, change your Apple password immediately.