An infiltrator gets US drone secrets
A basic security gap used to access very sensitive files related to the US Army's military spy planes, and the security company Recorded Future said it had discovered an attempt to sell this secret information for a few hundred dollars in a forum on the Internet last month, as it included the documents that were doneAnnouncing it for $ 150 and 200 dollars, technical details of the MQ-9 Reaper plane.
This drone was used within the uninhabited control tasks of the army and other organizations, including border monitoring, and the company claims that the evidence and maintenance brochures and a list of employees who were assigned to work to repair this type of aircraft have been sold, as the information has been revealed after thatTwo US military personnel have contacted the Internet through Netgear.
These routers seem to use virtual login settings, and this was discovered within the routers for the first time in two years, and their fixed bars have not yet been updated, and Andrei Barysevich, a dark web expert within the RECORDED FUTURE company, says thatSome documents were taken from the computers of a captain in the Air Force working at a base in Nevada.
He added that the infiltrator had the right to access to a wide range of CCTV direct surveillance cameras, including those installed on surveillance aircraft and the border between the United States and Mexico, checkpoints, highways and plane that wipe the Gulf of Mexico.

One of those files that was discovered was a testimony stating that the captain had successfully completed cybersecurity training, and there are documents related to the maintenance of the M1 Abrams, and details of how to defend against the bombing and explosive devices that are being offered for sale.
The files were announced for sale through a dark web forum, and the company believes that no one bought the documents, and it refrained from providing the alleged infiltrators account or the forum that the details were announced within, saying that it continues to work with the law enforcement agencies, with a hundred percent confirmed that the documents thatIt has been announced for real sale.
The security researcher says that he started talking to the infiltrator through the dark web forum, but he moved to the application of an encrypted correspondence to display samples of documents, and these documents included possible photos taken by drones and technical documents of other military equipment, and Andre Parisific added that after a short time of communicationThe company, with law enforcement and passing information to the Air Force, deleted the infiltrat.
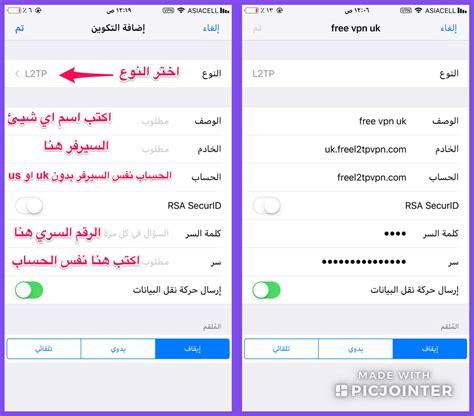
He explained that he does not know how much the data obtained by the infiltrator because he claimed to have a weak internet connection and as a result, he claimed that he did not download everything available, and Andre Parisific says that the infiltrator examined the Shodan search engine, which displays the devices connected to the Internet, to search for guidance devicesNetgear whose default details have not been updated, and as soon as the location of the device is located, it can be accessed remotely and can access the FTP file transmission protocol using the username "ADMIN" and the password "Password".
Recorded Future pointed out that the survey processed by the Shodan search engine revealed 4000 devices that can be penetrated using this method, as this number decreased from the 6000 which was present when the problem was reported for the first time in 2016, and Shodan search operations did not appearOnly the currently active devices and connected to the Internet.
Cyber security officials in the United Kingdom and the United States issued a joint warning to individuals and companies that highlight their belief that the routers, in addition to other technical equipment, were hacked by Russian infiltrators, where millions of devices were targeted through attacks, and it wasIt is possible to steal intellectual property, and according to information, routers have been targeted to form a basis for future offensive operations.
Harmical software bearing the name VPNFilter was found in more than 500,000 routers, and this malware, which was first discovered by CISCO, has the ability to close the router and kill the Internet connection, and Cisco explained inMay this year that the behavior of these harmful software on network equipment is particularly worry.
This incident is the latest for unsafe routers, which leads to security weaknesses, as these continuous security gaps clearly show how connected routers can pose a real danger, as the infiltrator targeting the US military was trying to penetrate these devices every day with the help of the engineSearch Shodan to get new victims, with the entire day spending the experiment of each router available through the search separately, in order to know if anything can be obtained.