5 ways to check your internet connection safety
With news about a large penetration that occurs almost every week during this year;It may be difficult to know if your data is safe, as hackers constantly seek to track user activity, steal their data or deceive them to reveal sensitive information to achieve financial gains.
Unfortunately;Most people do not know that they have been hacked until it is too late, so with the many electronic security crimes you must check the weaknesses of the network that you use constantly to secure yourself from pirate attacks, and protect your privacy on the Internet.
Here are 5 ways to help you check your internet connection safety:
1- Wall to protect the protection wall to search for weaknesses:
Firewall is one of the important tools to maintain the safety of your devices, even if the pirates can know your site and the IP address of your device, the protection wall prevents them from accessing the operating system and the network, and it can help prevent the spread of harmful programs.
It is worth noting that the Windows operating systems (Windows) and the modern MacOS MacOS contain integrated protection walls to define the outgoing and incoming Internet outlets, and there are also many external programs that exceed these compact programs in terms of features and ease of use.
You can use one of the services such as: Shieldup!To check the safety wall on your devices, if your protection wall does not provide you with the necessary protection, then it is worth trying a safer wall.

2- Test the strength of the anti-virus program:
Anti -virus programs work to examine files as soon as they are downloaded, and to ban files suspected of being viruses to ensure that there are no harmful files that may affect the operating system, so it must be verified that they work properly, as the weak antivirus program will not discover threats as soon as they appear,It may expose you to a security threat.
To test the antivirus program on your device;You can download the EICAR file, as EICAR files are originally not harmful, but antivirus programs discover them as if they were a virus.You can also press it in the Zip file as an attempt to hide it from antivirus programs, and this is a great way to anti -virus test without exposing the computer to actual threats.
3- Check the website protocol during browsing:
When downloading a web site uses the HTTP protocol, your connection to the site is not encrypted, and this means that anyone on the network can see your information, or even modify the contents of the site before it reaches you, but if the site uses the HTTPS protocol your connection will be encrypted, and accordingly it isYour personal data (such as passwords, or credit card information) will be protected when sent to the site.
You can learn if the web site uses the HTTPS protocol by looking at the URL;You should start with "https" if your connection is safe, and some web browsers may display a symbol next to the address bar to inform you of encryption your data, for example, the Google Chroming browser will show a small lock to inform you that the site uses https, or a red mark on non -encrypted sites that use the HTTP protocol.
When logging in to any website, be sure to review the protocol that it uses, if it uses https, it is safe and you can log in, and for more insurance you can use the HTTPS everywhere adding that allows you to encrypt your connections with many major sites, which makes browsing the Internet moreSafety, it is available for most common web browsers.
4- Securing the router:
Your router is the main axis of internet connection in your home, which makes it a major purpose for the pirates to steal data or steal the Internet frequency, which leads to slowing the Internet speed and consuming more data.So securing it is important to everyone.
You should make sure that the wireless network encryption at home using the WPA2 AES protocol, and it takes only about 30 seconds to activate the encryption protocol in your router settings, all it has to do is go to the steering settings of the router, and next to the Network Authentision option;Make sure to activate the WPA2 safety standard.
If this is not available, choose the WPA standard, but do not use the WeP standard because it is weak and can be easily penetrated even by the novice infiltrators.
Once the WPA / WPA safety standard is set, make sure you use AES instead of TKIP, because AES is more modern and safe, and most importantly when activating WPA2, be sure to use a strong password, difficult to guess from external ends.
For more safety;Many routers come with a default SSID name that can bear the brand name, or model, and if the pirates know your router type, it will become easier for them to penetrate it, so the default SSID name must be changed.
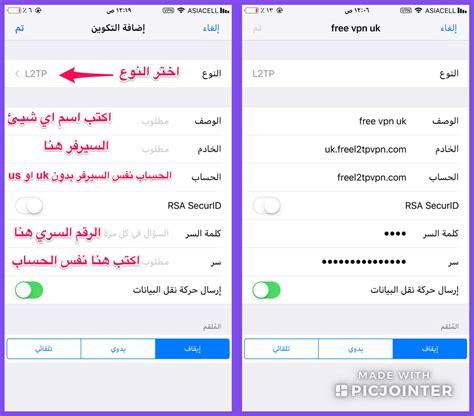
5- VPN verification:
VPN (virtual network) services allow you to automatically encrypt your data, especially in the event of the use of public Wi-Fi networks, or the use of banking services via the Internet, or other sites that contain special data.
If you use a VPN service;You can check its strength with the IP League service, which allows you to check your connection to ensure that your VPN connection is safe, and does not reveal your real data while using the Internet, and if you visit the website without the VPN service, it will offer you all the information about the IP addressWith your device, your geographical locations, as is evident in the following image: